AWS Security – Resource Protection
by Will Chalmers

In the previous security blog post, we discussed some core security practices everyone should apply to their AWS account. We will move on to the resources and some critical fundamental security practices you should be using – no matter the size or scale of your workload.
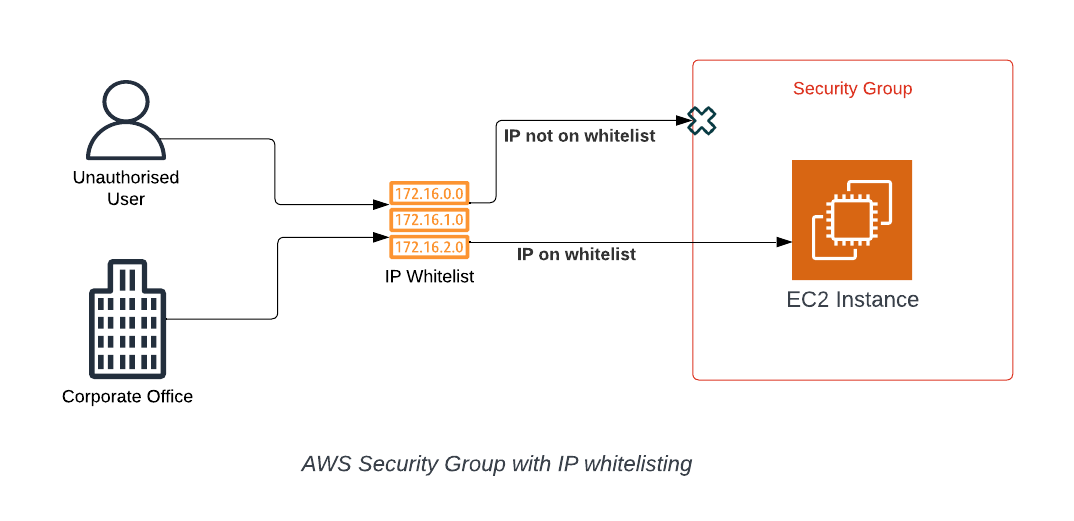
Security Groups
Security Groups act like a firewall for your compute resources. They restrict access & ports to specific IP addresses. Having certain ports available for everyone to use is expected and required for many web applications, such as websites, where port 80/443 must be open for the public to access the website.
However, ports that allow users to connect to the server behind the website are where you can run into issues. Port 22 (SSH) and 3389 (RDP) are commonly used for Linux and Windows servers, respectively. It’s important to have sensitive ports such as these restricted to only IP addresses you know, for example, an office IP range.
Overall, this adds a layer of security to your compute resources, stopping potential attackers from touching the server unless they are at your corporate office or another verified location.
S3 Bucket Protection
S3 Buckets act as a virtual storage container for your data. Configuring strict access controls ensures that only authorized users or systems can access its contents. By correctly configuring precise bucket policies and permissions, you establish a digital perimeter only authorized users or applications can breach. This safeguards your data from inadvertent exposure and prevents potential cyberattacks.
S3 Bucket policies should have all public access restricted on them. This should be done through both the Bucket Policy and the BlockPublicAccess settings.
Enabling encryption (which we will discuss later in the article) for S3 buckets is similar to installing a strong lock on your digital vault. Setting it as a default in your AWS account ensures automatic data encryption, enhancing security on all data inside the bucket, as encryption will render the files unreadable unless the recipient also has the decryption keys.
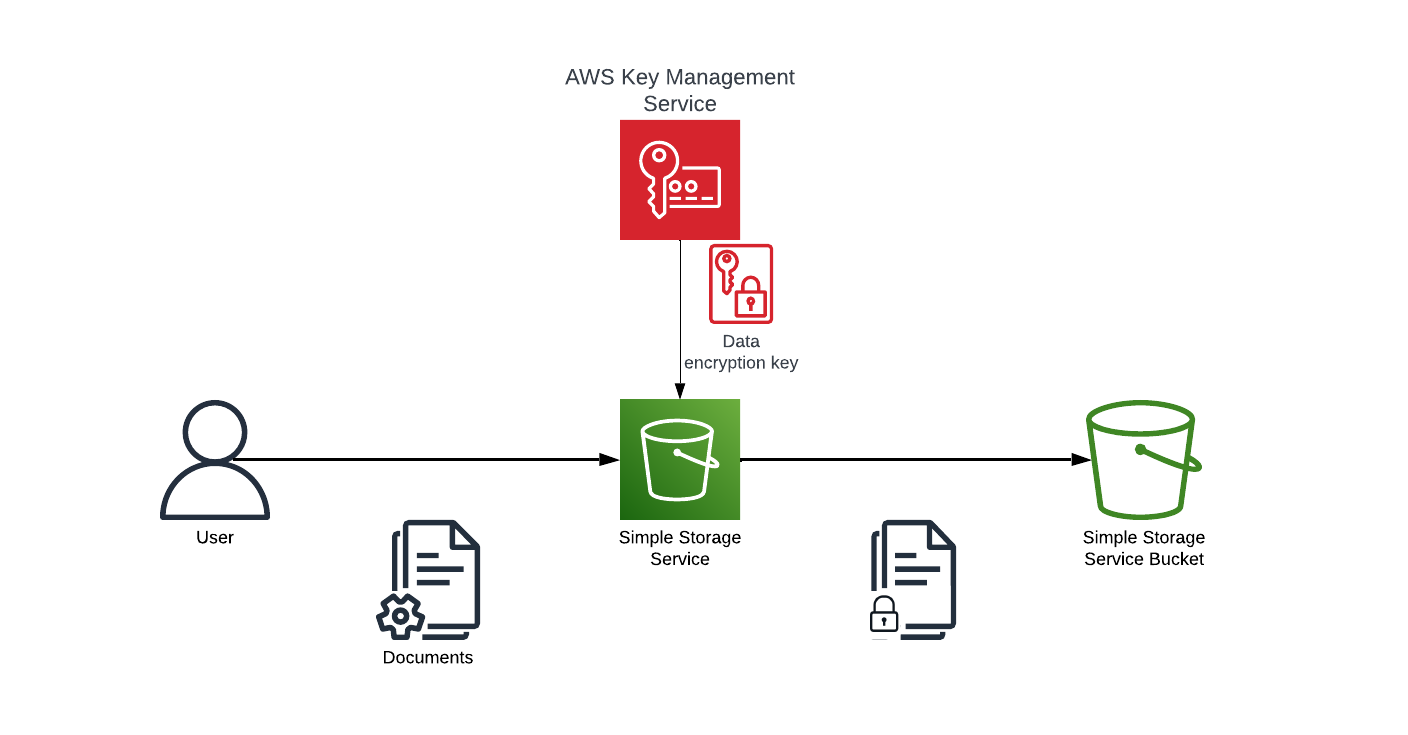
Encryption, Encryption, Encryption…
Enabling encryption for all resources whenever possible is a non-negotiable security measure in today’s digital landscape. It ensures that the data remains unreadable even if unauthorized access occurs without the encryption keys. This protects sensitive information, mitigates data breaches, and helps maintain compliance with data protection regulations. Encryption is an essential safeguard for your digital assets, and making it a default practice fortifies your overall cybersecurity posture.
This can be achieved easily within AWS as most services come with a simple checkbox you need to select, and AWS will ensure that all your data is encrypted for that specific resource.
Auditing
Consistently monitoring & auditing your AWS users and resources is essential because it helps you detect and investigate security breaches, ensure regulatory compliance, and maintain a comprehensive record of changes and actions within your AWS environment.
Many AWS services are dedicated to helping with the security and auditing of your resources. Listed below are some of the most popular ones that can be used to take your AWS security to the next level
- AWS Config: Continuously monitors and records your AWS resource configurations, allowing you to assess, audit, and maintain compliance with your desired configurations and security policies.
- AWS CloudTrail: provides detailed logs of AWS API activity in your account, helping you maintain security and compliance by tracking changes and user actions.
- AWS Key Management Service (KMS): Managed service that allows you to create and control encryption keys for securing your data and resources in the AWS cloud.
Cost
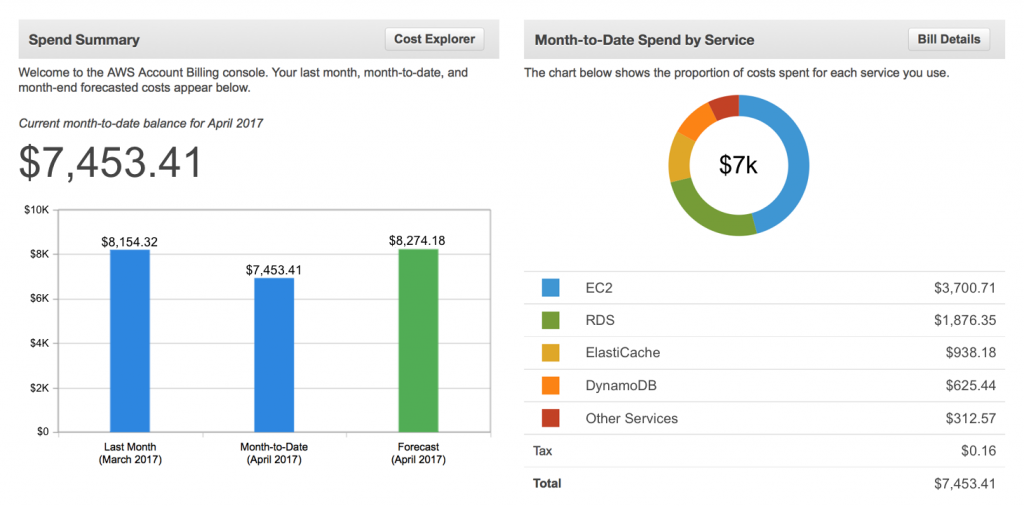
Monitoring your AWS costs and setting up billing alarms is crucial for keeping your cloud expenses in check and avoiding unexpected budget overruns. By regularly tracking your AWS spending, you can gain insights into where your resources are being allocated and identify opportunities for cost optimization. Billing alarms serve as an early warning system, notifying you when your spending exceeds predefined thresholds and allowing you to take proactive measures to control costs.
This financial visibility helps maintain your budget and ensures that your AWS resources are used efficiently, contributing to a more cost-effective and sustainable cloud infrastructure.
While this article goes through some basic steps for increasing account security, it does not stop here. Security is an ever-evolving topic that constantly requires reviews, remediations and further actions to keep your account safe. Implementing the recommendations made in this article will harden your AWS accounts, but this should also serve as a starting point on your security journey.
If you’re short on time or expertise, reach out to us via email to hear more about our pre-packaged security services!